Helping You to Explore More in Information Technology
Get Expert Online Technical Tips Delivered Right to your Inbox!

Popular Articles
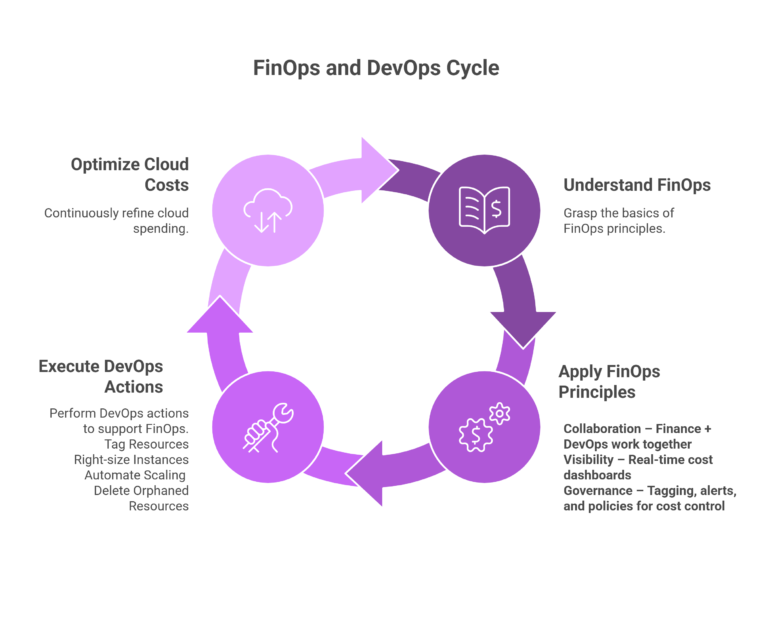
What is FinOps? FinOps (Financial Operations) is a cultural practice that brings together Finance, Engineering, and Business teams to optimize cloud spending through...
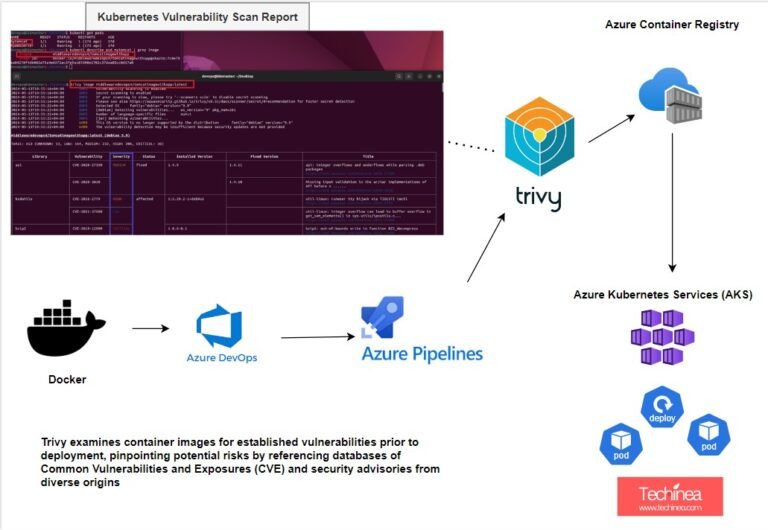
https://youtu.be/j14w3X1kRQg Welcome to our comprehensive guide on Kubernetes security! In this tutorial, we’ll walk you through the process of installing Trivy, a...
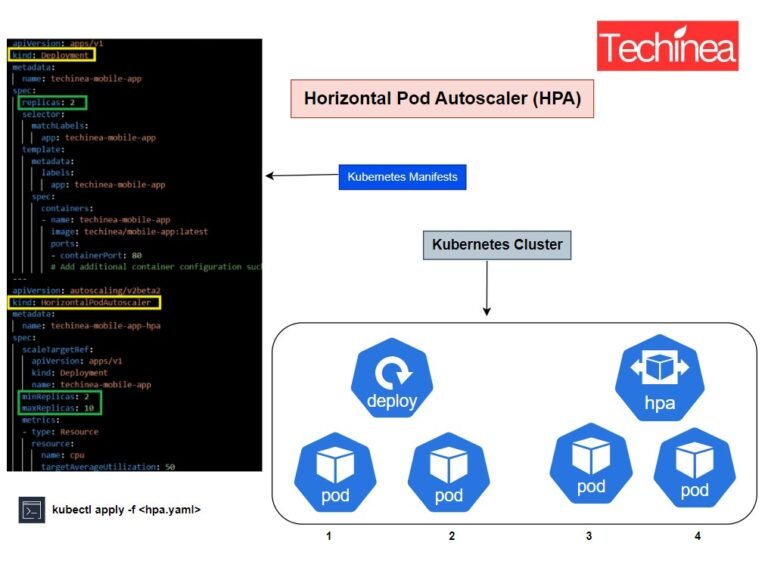
Kubernetes Horizontal Pod Autoscaler (HPA): Detailed Explanation In Kubernetes, the Horizontal Pod Autoscaler (HPA) is a resource that automatically adjusts the number of...
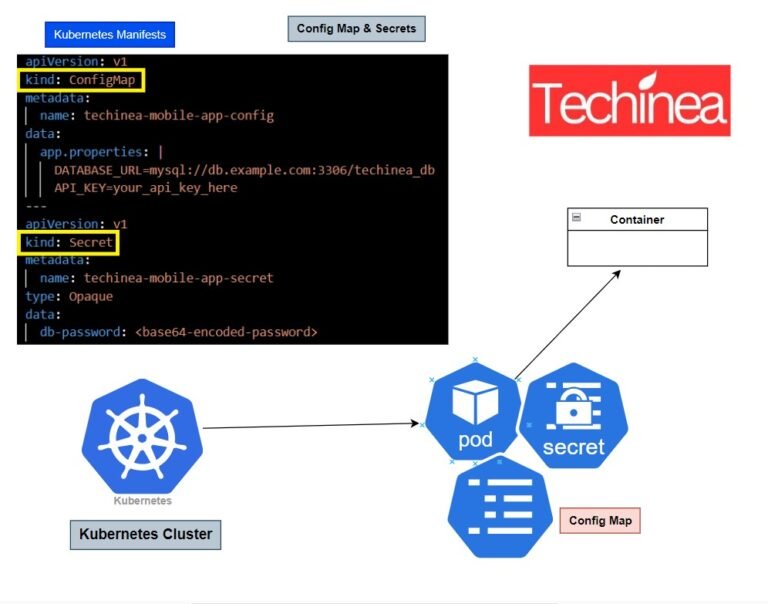
Kubernetes ConfigMaps and Secrets: Detailed Explanation In Kubernetes, ConfigMaps and Secrets are resources used to manage configuration data and sensitive information...
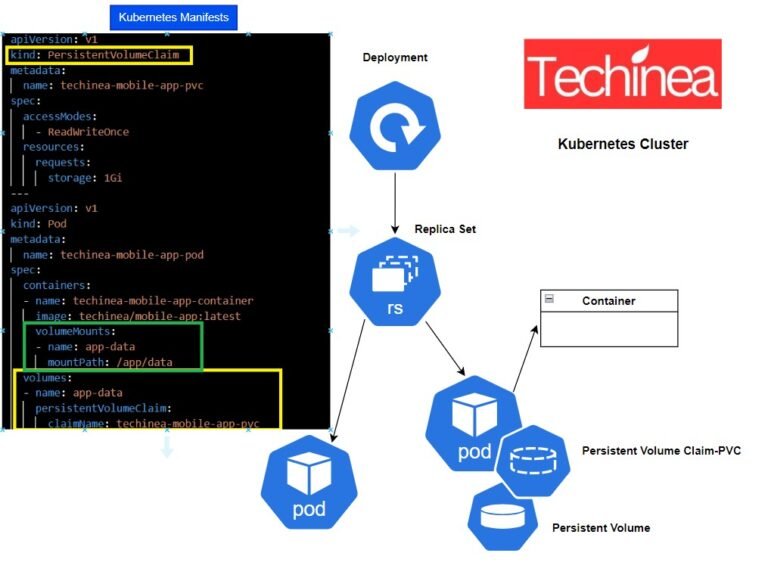
Kubernetes Volumes: Detailed Explanation In Kubernetes, volumes provide a way to persist and share data between containers within pods. They enable applications to store...
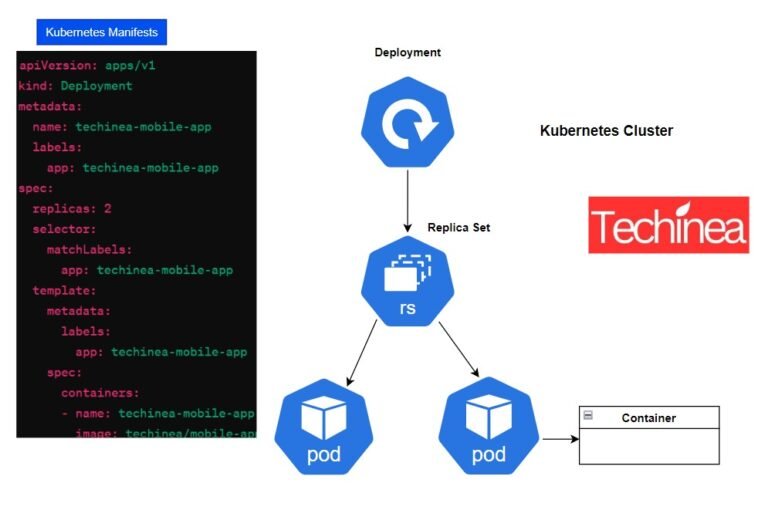
Kubernetes Deployments: Detailed Explanation In Kubernetes, Deployments are a high-level resource that enables declarative updates to applications deployed within a...
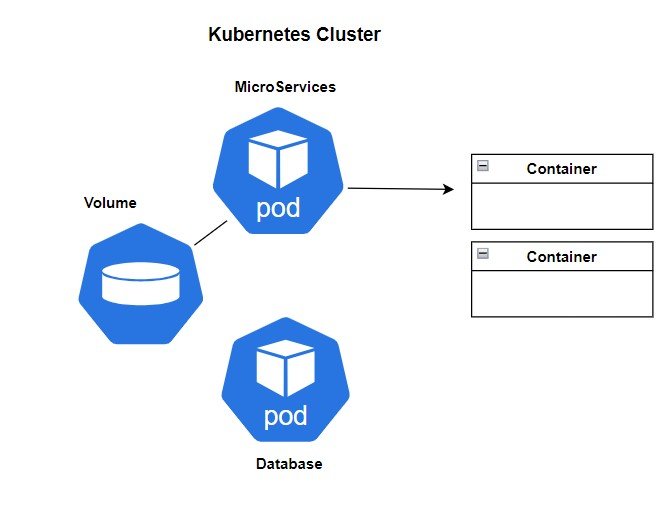
Kubernetes Pods: Detailed Explanation In Kubernetes, a pod is the smallest deployable unit that represents a single instance of a running process within a cluster. It...
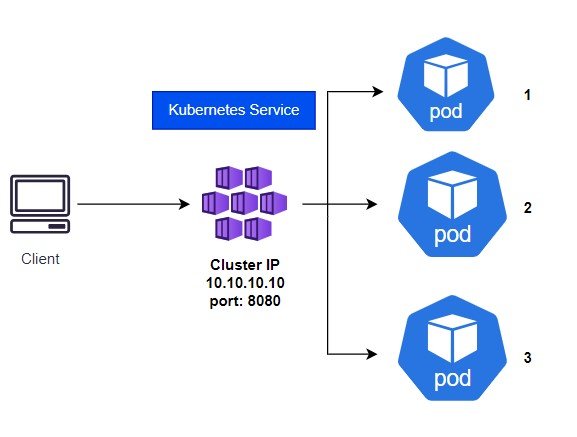
Kubernetes services play a role in facilitating communication between various components (such as pods) within a Kubernetes cluster. They provide a consistent way to...
Issue-1: failed to deploy kubernete stack: failed to execute kubectl command: “The Deployment “TechineaMobileApp” is invalid: metadata.name: Invalid...