Output (After Scanninng):
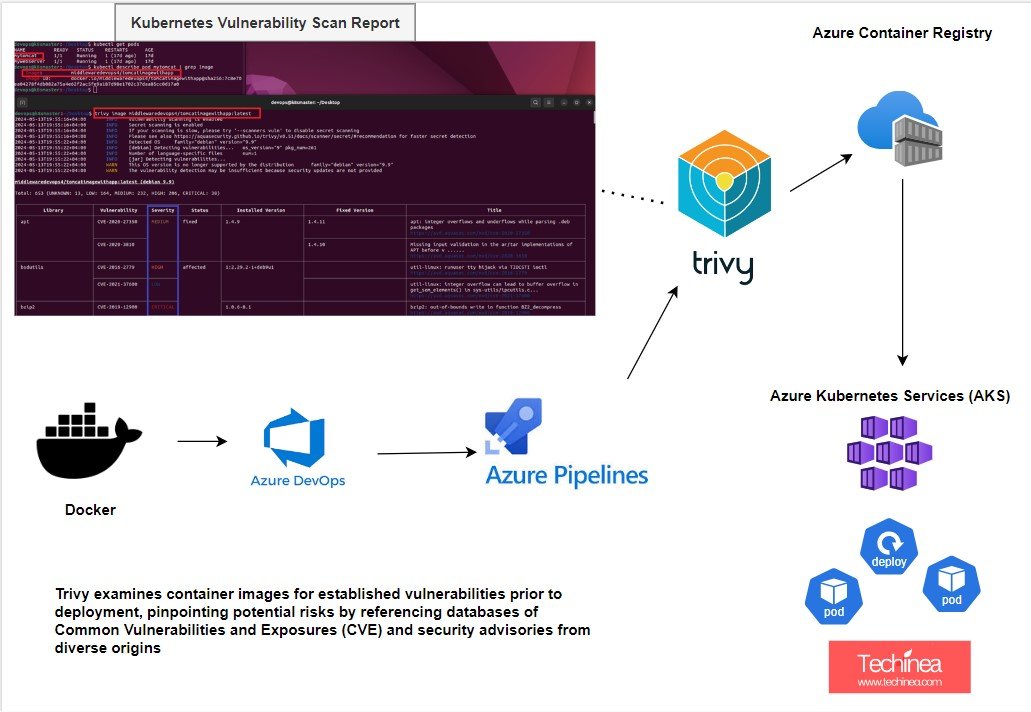
command used to scan: trivy image middlewaredevops4/tomcatimagewithapp:latest
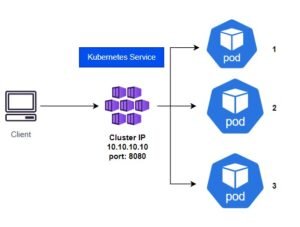
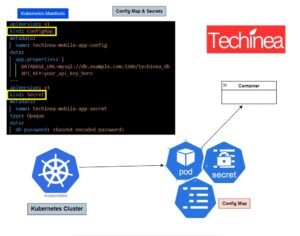
Kubernetes security explained by Trivy installation for Docker image scanning comes under Container security in Kubernetes vulnerability scanning. it will be Kubernetes best practices and Docker security tools,Kubernetes security tools
This Kubernetes tutorials explains about Docker image vulnerability scanning using trivy for Kubernetes deployment security,Kubernetes security automation,Kubernetes security scanning tools,Docker container security,Kubernetes security checklist
#KubernetesSecurity #Trivy #TrivyScanner #DockerImages #ContainerSecurity #CyberSecurity #DevOps #K8s #VulnerabilityScanning #YouTubeTutorial #TechTutorial #CyberSecTutorial
To Explore More in DevSecOps- Read More :
Roles and Responsibilities of DevSecOps Engineer
DevSecOps Tool-Static Application Security Testing (SAST) tools
DevSecOps Tool-Dynamic Application Security Testing (DAST) Tools
DevSecOps Tool-Software Composition Analysis (SCA) Tools
DevSecOps Tool-Container Security Tools in DevSecOps
DevSecOps Tool-Infrastructure as Code (IaC) security Tools
DevSecOps Tools – Secrets Management Tools
DevSecOps Tools – Vulnerability Management Tools
DevSecOps Tools – Security Orchestration, Automation, and Response (SOAR) Tools
DevSecOps Tools – Security Information and Event Management (SIEM) tools