Infrastructure as Code (IaC) security focuses on securing the code and configurations used to automate the provisioning and management of infrastructure resources. IaC allows developers and operations teams to define infrastructure configurations as code, typically using declarative or imperative programming languages. Ensuring the security of these infrastructure definitions is crucial for maintaining the security of the entire system.
Examples:
Bridgecrew
Checkov
TerraScan
Here’s a detailed explanation of IaC security and its uses, along with a diagram illustrating the process:
Lets discuss about How IaC Security Works:
Secure Coding Practices: IaC templates should follow secure coding practices to prevent common security vulnerabilities. This includes avoiding hard-coded secrets, implementing least privilege access controls, and using parameterization to avoid injection attacks.
Static Analysis: Static analysis tools scan IaC code for security vulnerabilities, misconfigurations, and compliance violations. These tools analyze the code syntax, structure, and logic to identify potential security issues before deployment.
Secrets Management: Secrets such as API keys, passwords, and cryptographic keys used in IaC templates should be securely managed and stored outside of the codebase. Secrets management tools securely store and inject secrets into the infrastructure at runtime, ensuring that sensitive information is not exposed in code repositories.
Configuration Validation: IaC configurations should be validated against security policies, best practices, and compliance requirements. Configuration validation tools enforce security policies, detect misconfigurations, and provide recommendations for remediation.
Change Management: Changes to IaC code should follow a formal change management process to ensure that security, compliance, and operational requirements are met. Version control systems track changes to the codebase, facilitate code reviews, and enforce approval workflows.
Uses of IaC Security:
Preventing Misconfigurations: IaC security helps prevent misconfigurations that can lead to security vulnerabilities, data breaches, and service outages. By enforcing secure coding practices and configuration best practices, IaC security mitigates the risk of misconfigurations in the infrastructure.
Ensuring Consistency: IaC security ensures consistency and repeatability in infrastructure deployments by defining infrastructure configurations as code. This reduces the likelihood of configuration drift, where inconsistencies between environments introduce security vulnerabilities and operational risks.
Automating Security Controls: IaC security automates the enforcement of security controls, compliance requirements, and best practices throughout the infrastructure lifecycle. Automation reduces manual errors, accelerates deployment times, and improves overall security posture.
Enabling Auditing and Compliance: IaC security provides visibility into infrastructure configurations, changes, and compliance status through auditing and logging. Audit logs track changes to the infrastructure, identify security events, and facilitate compliance audits and investigations.
Integrating with CI/CD Pipelines: IaC security integrates with CI/CD pipelines to automate security testing, validation, and enforcement as part of the software delivery process. Integration with CI/CD pipelines ensures that security is integrated early in the development lifecycle and remains consistent across environments.
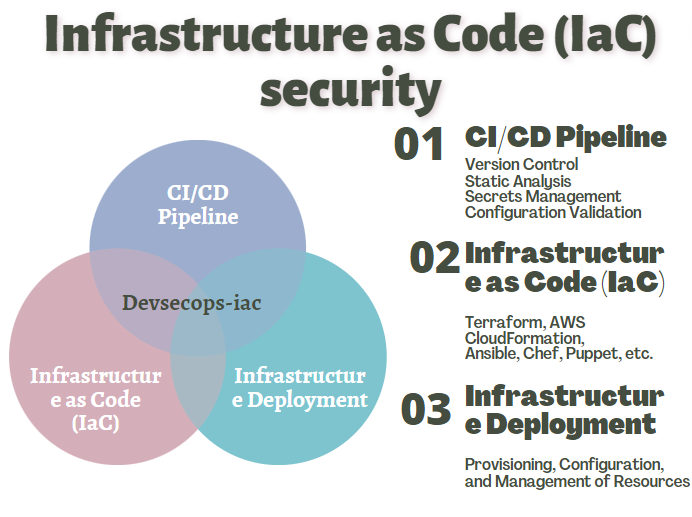
In this diagram:
CI/CD pipelines automate the development, testing, and deployment of IaC templates, integrating security testing, version control, static analysis, secrets management, and configuration validation.
Infrastructure as Code (IaC) templates define infrastructure configurations as code, allowing for consistent and repeatable provisioning and management of resources.
Infrastructure deployment tools (e.g., Terraform, AWS CloudFormation, Ansible) execute IaC templates to provision, configure, and manage infrastructure resources based on the defined specifications.
Overall, IaC security ensures that infrastructure configurations are secure, compliant, and consistent across environments, reducing the risk of security vulnerabilities and operational issues in cloud and hybrid IT environments.
To Explore More in DevSecOps- Read More :
Roles and Responsibilities of DevSecOps Engineer
DevSecOps Tool-Static Application Security Testing (SAST) tools
DevSecOps Tool-Dynamic Application Security Testing (DAST) Tools
DevSecOps Tool-Software Composition Analysis (SCA) Tools
DevSecOps Tool-Container Security Tools in DevSecOps
DevSecOps Tool-Infrastructure as Code (IaC) security Tools
DevSecOps Tools – Secrets Management Tools
DevSecOps Tools – Vulnerability Management Tools
DevSecOps Tools – Security Orchestration, Automation, and Response (SOAR) Tools
Identity and Access Management-(IAM) in DevSecOps
DevSecOps Tools – Security Information and Event Management (SIEM) tools