Identity and Access Management (IAM) in DevSecOps refers to the processes, technologies, and policies used to manage and secure digital identities and control access to resources within an organization’s IT environment. IAM plays a crucial role in ensuring that only authorized users and systems have access to the right resources at the right time, while also maintaining security, compliance, and operational efficiency. In DevSecOps, IAM is essential for securely managing identities and access privileges across the software development lifecycle. Let’s explore IAM in detail, including its key components, benefits, popular tools, and a diagram illustrating its workflow in DevSecOps.
Key Components of IAM:
Authentication: IAM systems authenticate the identity of users and systems seeking access to resources. This process typically involves verifying credentials such as usernames, passwords, biometric data, or cryptographic keys.
Authorization: Once authenticated, IAM systems authorize users and systems based on predefined access policies and permissions. Authorization determines what resources a user or system is allowed to access and what actions they can perform.
Directory Services: IAM solutions often integrate with directory services such as Active Directory (AD) or Lightweight Directory Access Protocol (LDAP) to manage user identities, roles, and access rights centrally.
Single Sign-On (SSO): SSO enables users to authenticate once and access multiple applications or services without needing to log in again. IAM solutions provide SSO capabilities to streamline user authentication and improve user experience.
Multi-Factor Authentication (MFA): IAM systems support MFA to add an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code sent to their mobile device.
Identity Lifecycle Management: IAM solutions manage the entire lifecycle of user identities, including provisioning, deprovisioning, and account management. This ensures that access privileges are granted and revoked in a timely manner as users join, move within, or leave the organization.
Benefits of IAM in DevSecOps:
Enhanced Security: IAM helps organizations strengthen security by ensuring that only authorized users and systems have access to resources. By enforcing least privilege access, IAM reduces the risk of unauthorized access and potential security breaches.
Improved Compliance: IAM solutions help organizations achieve and maintain regulatory compliance by enforcing access controls, auditing access activities, and providing detailed reports on user access rights and permissions.
Operational Efficiency: IAM streamlines identity and access management processes, such as user provisioning and deprovisioning, access requests, and password management. This improves operational efficiency and reduces administrative overhead.
Centralized Management: IAM solutions provide centralized management of user identities, access policies, and authentication mechanisms. This centralized approach simplifies administration, improves visibility, and enhances governance.
Integration with DevOps Tools: IAM integrates seamlessly with DevOps tools and platforms to automate identity and access management processes within the DevSecOps pipeline. This ensures that security controls are applied consistently throughout the software development lifecycle.
Popular IAM Tools:
Okta: Okta is a cloud-based IAM platform that provides authentication, SSO, and identity lifecycle management capabilities. It integrates with a wide range of applications and services and offers advanced security features such as adaptive authentication and MFA.
Microsoft Azure Active Directory (Azure AD): Azure AD is Microsoft’s cloud-based IAM service that provides identity and access management for Azure cloud services and Microsoft 365 applications. It offers SSO, MFA, conditional access policies, and integration with on-premises Active Directory environments.
Ping Identity: Ping Identity is an IAM platform that provides authentication, SSO, and identity governance capabilities. It supports hybrid IT environments and offers features such as federated identity management, API security, and adaptive authentication.
ForgeRock Identity Platform: ForgeRock is an open-source IAM platform that offers identity and access management, SSO, and identity governance solutions. It provides support for modern authentication standards such as OAuth 2.0 and OpenID Connect.
AWS Identity and Access Management (IAM): AWS IAM is a cloud-native IAM service provided by Amazon Web Services (AWS). It enables organizations to manage user identities and access permissions for AWS services and resources securely.
Diagram:
Identity Lifecycle Management (IAM): IAM manages the entire lifecycle of user identities, including provisioning, deprovisioning, and account management.
Authentication and SSO: IAM authenticates user identities and provides SSO capabilities, allowing users to access multiple applications with a single set of credentials.
Authorization and Access: the iam enforces access controls and also permissions based on predefined policies, determining what resources users can access and what actions they can perform.
Multi-Factor Authentication (MFA): IAM supports MFA to add an extra layer of security by requiring users to provide multiple forms of authentication.
Integration with DevOps Tools: IAM integrates seamlessly with DevOps tools and platforms, ensuring that security controls are applied consistently throughout the DevSecOps pipeline.
Continuous Monitoring and Security Policy Enforcement: IAM continuously monitors user access activities and enforces security policies to detect and respond to security threats proactively.
Conclusion:
IAM is a critical component of DevSecOps, providing the foundation for securely managing user identities and controlling access to resources across the organization’s IT environment. By implementing IAM solutions, organizations can enhance security, improve compliance, streamline operations, and integrate security controls seamlessly into the DevSecOps pipeline. Through centralized management, automation, and continuous monitoring, IAM helps organizations achieve greater visibility, control, and resilience in the dynamic landscape of modern software development
To Explore More in DevSecOps- Read More :
Roles and Responsibilities of DevSecOps Engineer
DevSecOps Tool-Static Application Security Testing (SAST) tools
DevSecOps Tool-Dynamic Application Security Testing (DAST) Tools
DevSecOps Tool-Software Composition Analysis (SCA) Tools
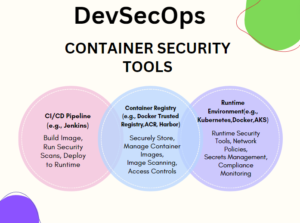
DevSecOps Tool-Container Security Tools in DevSecOps
DevSecOps Tool-Infrastructure as Code (IaC) security Tools
DevSecOps Tools – Secrets Management Tools
DevSecOps Tools – Vulnerability Management Tools
DevSecOps Tools – Security Orchestration, Automation, and Response (SOAR) Tools
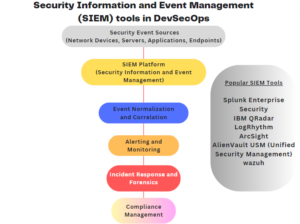
DevSecOps Tools – Security Information and Event Management (SIEM) tools