Kubernetes ConfigMaps and Secrets: Detailed Explanation
In Kubernetes, ConfigMaps and Secrets are resources used to manage configuration data and sensitive information, respectively. They provide a way to decouple configuration from containerized applications, making it easier to manage and update configuration settings without modifying application code or container images.
Kubernetes ConfigMaps:
Purpose: ConfigMaps is used to store non-sensitive data likes configuration data, such as environment variables, command-line arguments, or configuration files, in key-value pairs.
Usage: ConfigMaps can be mounted as volumes or passed as environment variables to containers within pods, allowing applications to access the configuration data.
Scenarios: ConfigMaps are commonly used to store application settings, database connection strings, URLs, and other configuration parameters that may vary between environments or deployments.
Kubernetes Secrets:
Purpose: Secrets are similar to ConfigMaps but are specifically designed for storing sensitive information, such as passwords, API keys, or TLS certificates.
Security: Secrets are base64-encoded by default when stored in Kubernetes, providing a basic level of security. However, it’s important to note that base64 encoding is not encryption, and secrets should be treated with care.
Usage: Secrets can be mounted as volumes or passed as environment variables to containers within pods, allowing applications to securely access sensitive data.
Scenarios: Secrets are commonly used to store credentials for accessing databases, APIs, or external services, as well as TLS certificates for securing communication between components.
Benefits of Using ConfigMaps and Secrets:
Separation of Concerns: ConfigMaps and Secrets allow configuration data and sensitive information to be managed separately from application code and container images, improving maintainability and flexibility.
Dynamic Updates: Changes to ConfigMaps and Secrets can be applied dynamically to running pods without requiring pod restarts, enabling real-time configuration updates and minimizing downtime.
Enhanced Security: Secrets provide a secure mechanism for storing sensitive data, ensuring that credentials and other sensitive information are not exposed in plain text within container images or configuration files.
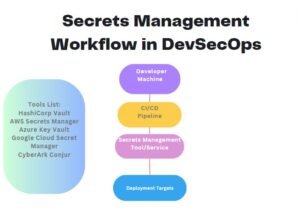
Diagram Illustrating ConfigMaps and Secrets:
In the diagram:
There are ConfigMaps and Secrets stored within the Kubernetes cluster.
ConfigMaps contain non-sensitive configuration data in key-value pairs.
Secrets contain sensitive information in key-value pairs (Note: Secrets are base64-encoded when stored).
Applications deployed within the cluster can access ConfigMaps and Secrets as volumes or environment variables, allowing them to retrieve configuration data and sensitive information as needed.
ConfigMaps and Secrets provide a flexible and secure way to manage configuration data and sensitive information in Kubernetes, enabling applications to be more portable, maintainable, and secure.
Below is a sample Kubernetes YAML file for deploying the “Techinea Mobile App” with ConfigMaps and Secrets:
In this YAML file:
We define a ConfigMap named
techinea-mobile-app-configcontaining configuration data for the “Techinea Mobile App”. The configuration data is stored in theapp.propertieskey-value pair format.We define a Secret named
techinea-mobile-app-secretcontaining sensitive information such as the database password. The password is base64-encoded for security.We define a Pod named
techinea-mobile-app-podthat runs the “Techinea Mobile App” container.We specify environment variables (
DATABASE_URL,API_KEY,DB_PASSWORD) for the container, with values retrieved from the ConfigMap and Secret using references (configMapKeyRef,secretKeyRef).
With this setup, the “Techinea Mobile App” pod will have access to configuration data from the ConfigMap and sensitive information from the Secret, allowing it to securely retrieve settings and credentials required for operation.
To Read More on Kubernetes Check Below
What is Kubernetes Deployments?
To Explore More in DevSecOps- Read More :
Roles and Responsibilities of DevSecOps Engineer
DevSecOps Tool-Static Application Security Testing (SAST) tools
DevSecOps Tool-Dynamic Application Security Testing (DAST) Tools
DevSecOps Tool-Software Composition Analysis (SCA) Tools
DevSecOps Tool-Container Security Tools in DevSecOps
DevSecOps Tool-Infrastructure as Code (IaC) security Tools
DevSecOps Tools – Secrets Management Tools
DevSecOps Tools – Vulnerability Management Tools
DevSecOps Tools – Security Orchestration, Automation, and Response (SOAR) Tools
DevSecOps Tools – Security Information and Event Management (SIEM) tools