Dynamic Application Security Testing (DAST) is a security testing methodology used to identify vulnerabilities in web applications by simulating attacks against a running application.
Here’s a detailed explanation of DAST and its uses, along with a diagram illustrating the process:
How DAST Works:
Black-Box Testing: DAST operates as a black-box testing technique, where the tester has no knowledge of the internal workings of the application. Instead, it interacts with the application’s exposed interfaces (e.g., web forms, APIs) just like a real-world attacker would.
Attack Simulation: DAST tools simulate various types of attacks, such as injection attacks (e.g., SQL injection, XSS), authentication bypass, parameter tampering, session management flaws, and more. These attacks are performed by sending malicious input to the application and analyzing its responses.
Dynamic Crawling: DAST tools crawl through the application’s accessible pages and endpoints to discover all available functionality. This includes following links, submitting forms, and interacting with APIs to map out the application’s attack surface.
Input Fuzzing: DAST tools fuzz input parameters with a variety of payloads, including SQL injection strings, XSS payloads, and other attack vectors. By sending different combinations of input data, DAST tools attempt to trigger vulnerabilities and identify potential security weaknesses.
Response Analysis: DAST tools analyze the responses received from the application to detect signs of security vulnerabilities. This includes examining HTTP headers, response codes, error messages, and content returned by the application.
Reporting: DAST tools generate detailed reports that highlight discovered vulnerabilities, including their severity, impact, and remediation recommendations. These reports help developers prioritize and address security issues in the application.
Uses of DAST:
Identifying Web Application Vulnerabilities: DAST is used to identify vulnerabilities in web applications, such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), insecure direct object references (IDOR), and more.
Validating Security Controls: DAST validates the effectiveness of security controls implemented in the application, such as input validation, authentication mechanisms, session management, access controls, and encryption.
Complementing SAST: DAST complements Static Application Security Testing (SAST) by identifying vulnerabilities that may not be apparent from the source code alone, such as configuration issues, runtime behavior, and integration vulnerabilities.
Detecting Runtime Vulnerabilities: DAST detects vulnerabilities that are only present in the running instance of the application, such as misconfigurations, runtime dependencies, and environmental issues.
Supporting Compliance Requirements: DAST helps organizations comply with industry regulations and security standards by identifying and remediating vulnerabilities that may violate compliance requirements, such as PCI DSS, GDPR, HIPAA, and others.
Integration into CI/CD Pipelines: DAST tools can be integrated into Continuous Integration/Continuous Deployment (CI/CD) pipelines to automate security testing as part of the software development process. This ensures that security vulnerabilities are identified and addressed early in the development lifecycle, reducing the time and effort required for manual security testing.
In this diagram:
The web application is scanned by the DAST tool, which performs dynamic crawling, input fuzzing, attack simulation, and response analysis.
The DAST tool generates a vulnerability assessment report, which includes details of discovered vulnerabilities, their severity, impact, and remediation recommendations.
The report is used by developers and security teams to prioritize and address security issues in the application.
Overall, DAST plays a crucial role in identifying vulnerabilities in web applications and helping organizations improve their security posture by addressing these vulnerabilities before they can be exploited by attackers.
To Explore More in DevSecOps- Read More :
Roles and Responsibilities of DevSecOps Engineer
DevSecOps Tool-Static Application Security Testing (SAST) tools
DevSecOps Tool-Dynamic Application Security Testing (DAST) Tools
DevSecOps Tool-Software Composition Analysis (SCA) Tools
DevSecOps Tool-Container Security Tools in DevSecOps
DevSecOps Tool-Infrastructure as Code (IaC) security Tools
DevSecOps Tools – Secrets Management Tools
DevSecOps Tools – Vulnerability Management Tools
DevSecOps Tools – Security Orchestration, Automation, and Response (SOAR) Tools
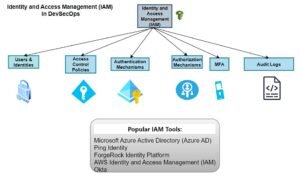
Identity and Access Management-(IAM) in DevSecOps
DevSecOps Tools – Security Information and Event Management (SIEM) tools