Software Composition Analysis (SCA) is a security testing methodology used to identify and manage open-source and third-party components (libraries, frameworks, modules, etc.) used in software applications. SCA tools analyze these components to identify known vulnerabilities, licensing issues, and other security risks. Here’s a detailed explanation of SCA and its uses, along with a diagram illustrating the process:
How SCA Works:
Component Identification: SCA tools identify and inventory all open-source and third-party components used in the application. This includes libraries, frameworks, modules, and dependencies declared in the application’s codebase, configuration files, and build scripts.
Vulnerability Detection: SCA tools compare the identified components against databases of known vulnerabilities, such as the National Vulnerability Database (NVD) or proprietary vulnerability databases maintained by the SCA tool vendors. They identify components with known vulnerabilities and provide information about the severity, impact, and remediation steps for each vulnerability.
License Compliance: These tools will analyze the licensing information associated with each component to ensure compliance with licensing requirements and obligations and also identify components with incompatible or restrictive licenses and provide recommendations for addressing licensing issues.
Version Management: SCA tools track the versions of components used in the application and alert developers to updates or patches available for components with known vulnerabilities. They provide information about the latest versions of components and guidance on upgrading to secure versions.
Policy Enforcement: SCA tools enforce organizational policies and guidelines related to the use of open-source components. They allow organizations to define policies for acceptable component versions, licensing requirements, vulnerability thresholds, and other criteria, and enforce these policies through automated checks and alerts.
Uses of SCA:
Identifying Vulnerabilities in Third-Party Components: SCA is used to identify known vulnerabilities in open-source and third-party components used in the application. By scanning the application’s dependencies, SCA tools help developers and security teams identify and remediate vulnerabilities that may pose security risks to the application.
Managing Licensing Risks: SCA helps organizations manage the risks associated with the use of open-source components by analyzing licensing information and ensuring compliance with licensing requirements. By identifying components with incompatible or restrictive licenses, SCA tools help organizations avoid legal and intellectual property issues.
Ensuring Supply Chain Security: SCA plays a crucial role in ensuring the security of the software supply chain by identifying and addressing security risks in third-party components. By scanning components for vulnerabilities, SCA tools help organizations mitigate the risk of supply chain attacks and prevent malicious actors from exploiting vulnerabilities in upstream dependencies.
Facilitating Risk-Based Decision Making: SCA provides organizations with insights into the security risks associated with the use of open-source components, allowing them to make informed decisions about risk acceptance, mitigation, and remediation. By prioritizing vulnerabilities based on severity, impact, and exploitability, SCA tools help organizations allocate resources effectively to address the most critical security issues.
Integrating with Development Workflows: SCA tools integrate with development workflows, including Continuous Integration/Continuous Deployment (CI/CD) pipelines and development environments, to automate security checks and provide real-time feedback to developers. By integrating SCA into the development process, organizations can identify and address security issues early in the software development lifecycle, reducing the risk of security breaches and costly remediation efforts.
In this diagram:
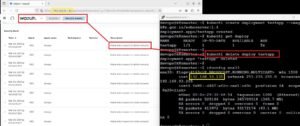
The SCA tool scans the software application to identify open-source and third-party components and performs vulnerability detection, license compliance checks, version management, and policy enforcement.
The SCA tool generates a report that provides details about discovered vulnerabilities, licensing information, and recommendations for addressing security and compliance issues.
The report is used by developers and security teams to prioritize and address security and compliance issues in the application’s dependencies.
Overall, SCA is a critical component of software security programs, helping organizations manage the risks associated with the use of open-source components and ensure the security and integrity of their software applications
To Explore More in DevSecOps- Read More :
Roles and Responsibilities of DevSecOps Engineer
DevSecOps Tool-Static Application Security Testing (SAST) tools
DevSecOps Tool-Dynamic Application Security Testing (DAST) Tools
DevSecOps Tool-Software Composition Analysis (SCA) Tools
DevSecOps Tool-Container Security Tools in DevSecOps
DevSecOps Tool-Infrastructure as Code (IaC) security Tools
DevSecOps Tools – Secrets Management Tools
DevSecOps Tools – Vulnerability Management Tools
DevSecOps Tools – Security Orchestration, Automation, and Response (SOAR) Tools
Identity and Access Management-(IAM) in DevSecOps
DevSecOps Tools – Security Information and Event Management (SIEM) tools