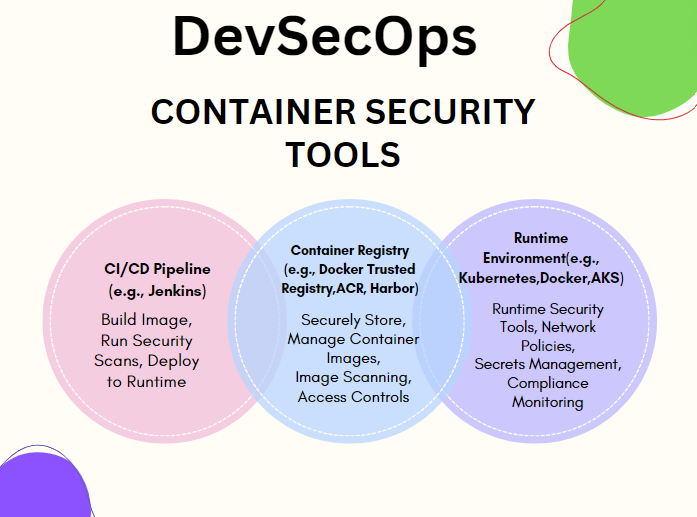
Container security tools in DevSecOps play a critical role in identifying, preventing, and mitigating security risks associated with containerized applications and the container runtime environment. These tools provide capabilities such as vulnerability scanning, runtime protection, secrets management, compliance monitoring, and more. Here’s a detailed explanation of container security tools and their uses, along with a diagram illustrating the process:
Common Container Security Tools:
Image Scanning Tools:
Purpose: Image scanning tools analyze container images for known vulnerabilities, outdated software components, and security misconfigurations.
Examples: Anchore Engine, Clair, Trivy, Twistlock, Aqua Security.
Runtime Security Tools:
Purpose: Runtime security tools protect running containers from unauthorized access, privilege escalation, and exploitation of vulnerabilities.
Examples: Falco, Sysdig Secure, Aqua Security, Twistlock, NeuVector.
Secrets Management Tools:
Purpose: Secrets management tools securely store and manage sensitive information, such as passwords, API keys, and cryptographic keys, and inject them into containers at runtime.
Examples: HashiCorp Vault, AWS Secrets Manager, Azure Key Vault.
Compliance Monitoring Tools:
Purpose: Compliance monitoring tools assess and enforce compliance with security policies, regulatory requirements, and industry standards throughout the container lifecycle.
Examples: Sysdig Secure, Aqua Security, Twistlock, Open Policy Agent (OPA).
Network Security Tools:
Purpose: Network security tools provide network segmentation, isolation, encryption, and policy enforcement to protect containerized applications from network-based attacks.
Examples: Calico, Cilium, Istio, Linkerd, Project Antrea.
Container Registry Tools:
Purpose: Container registry tools securely store and manage container images, enforce access controls, and integrate with CI/CD pipelines for image scanning and deployment.
Examples: Docker Trusted Registry, Harbor, Amazon ECR, Google Container Registry.
Orchestration Platform Security Features:
Purpose: Container orchestration platforms provide built-in security features, such as RBAC (Role-Based Access Control), network policies, admission controllers, and pod security policies.
Examples: Kubernetes, Docker Swarm, Amazon ECS, Google Kubernetes Engine (GKE).
Uses of Container Security Tools:
Vulnerability Management: Container security tools identify vulnerabilities in container images and runtime environments, enabling organizations to remediate security issues before deployment.
Runtime Protection: Runtime security tools protect running containers from unauthorized access, privilege escalation, and exploitation of vulnerabilities, reducing the risk of security breaches and data leaks.
Secrets Management: Secrets management tools securely store and manage sensitive information, ensuring that secrets are securely delivered to running containers and protected from unauthorized access.
Compliance Monitoring: Compliance monitoring tools assess and enforce compliance with security policies, regulatory requirements, and industry standards throughout the container lifecycle, reducing the risk of compliance violations and penalties.
Network Security: Network security tools provide network segmentation, isolation, encryption, and policy enforcement to protect containerized applications from network-based attacks, ensuring the confidentiality and integrity of data in transit.
Integration with CI/CD Pipelines: Container security tools integrate with CI/CD pipelines and development workflows to automate security checks, vulnerability scanning, and compliance assessments, ensuring that security is an integral part of the software development process.
In this diagram:
Container images are built, scanned for vulnerabilities, and securely stored in a container registry.
CI/CD pipelines automate the build process and integrate security scans to ensure that container images are free from vulnerabilities and compliance issues.
Immutable container images are deployed to runtime environments, where runtime security tools, network policies, secrets management, and compliance monitoring tools protect running containers and enforce security policies.
Overall, container security tools in DevSecOps enable organizations to effectively manage the security risks associated with containerized applications and ensure the security, compliance, and integrity of their software deployments.
To Explore More in DevSecOps- Read More :
Roles and Responsibilities of DevSecOps Engineer
DevSecOps Tool-Static Application Security Testing (SAST) tools
DevSecOps Tool-Dynamic Application Security Testing (DAST) Tools
DevSecOps Tool-Software Composition Analysis (SCA) Tools
DevSecOps Tool-Container Security Tools in DevSecOps
DevSecOps Tool-Infrastructure as Code (IaC) security Tools
DevSecOps Tools – Secrets Management Tools
DevSecOps Tools – Vulnerability Management Tools
DevSecOps Tools – Security Orchestration, Automation, and Response (SOAR) Tools
Identity and Access Management-(IAM) in DevSecOps
DevSecOps Tools – Security Information and Event Management (SIEM) tools