Wazuh is a popular open-source security monitoring platform that can be integrated into DevOps and Kubernetes environments to enhance security posture. (What is Wazuh-Read More)
Its role in these environments can be defined as follows:
Intrusion Detection and Prevention: Wazuh provides real-time threat detection and response capabilities, helping to identify and mitigate security incidents within DevOps and Kubernetes clusters. It can monitor logs, configurations, file integrity, and network traffic to detect suspicious activities or potential security breaches.
In this, we will see
Auditing Kubernetes with Wazuh
Installation of Wazuh-All in One(Quick install) in ubuntu:
–
sudo apt update
sudo apt install curl
You need to be the root user or a high-privileged user to run all commands described below — sudo su
curl -sO https://packages.wazuh.com/4.7/wazuh-install.sh && sudo bash ./wazuh-install.sh -a
Configure the Wazuh server for Kubernetes Integration
We need to create a webhook listener on the Wazuh server to receive the Kubernetes audit logs. For that we first create certificates for encrypted communication between the Wazuh server and the Kubernetes cluster and then create the webhook listener that listens on port 8080 and forwards the logs received to the Wazuh server for analysis. Also additionally, we create a systemd service to run the webhook listener, and enable the service to run on system reboot.
Create certificates for communication between the Wazuh server and Kubernetes
1. Create the directory to contain the certificates
mkdir /var/ossec/integrations/kubernetes-webhook/
2. Create a certificate configuration file /var/ossec/integrations/kubernetes-webhook/csr.conf and add the following. Replace <wazuh_server_ip> with your Wazuh server IP address
3. Create the root CA public and private keys
openssl req -x509 -new -nodes -newkey rsa:2048 -keyout /var/ossec/integrations/kubernetes-webhook/rootCA.key -out /var/ossec/integrations/kubernetes-webhook/rootCA.pem -batch -subj “/C=US/ST=California/L=San Jose/O=Wazuh”
4. Create the certificate signing request (csr) and the server private key
5. Generate the server certificate
openssl x509 -req -in /var/ossec/integrations/kubernetes-webhook/server.csr -CA /var/ossec/integrations/kubernetes-webhook/rootCA.pem -CAkey /var/ossec/integrations/kubernetes-webhook/rootCA.key -CAcreateserial -out /var/ossec/integrations/kubernetes-webhook/server.crt -extfile /var/ossec/integrations/kubernetes-webhook/csr.conf -extensions v3_req
Create the webhook listener
1. Install the Python flask module with pip. This module is used to
create the webhook listener and to receive JSON POST requests
/var/ossec/framework/python/bin/pip3 install flask
2. Create the Python webhook listener /var/ossec/integrations/custom-webhook.py. Replace <wazuh_server_ip> with your Wazuh server IP address
3. Create a systemd service at /lib/systemd/system/wazuh-webhook.service
4. Reload systemd, enable and start the webhook service
systemctl daemon-reload
systemctl enable wazuh-webhook.service
systemctl start wazuh-webhook.service
systemctl status wazuh-webhook.service
Enable access to port 8080 if the firewall on the Wazuh server is running
Configure Kubernetes audit logging on the master node
1. Create a policy file /etc/kubernetes/audit-policy.yaml to log the events
2. Create a webhook configuration file /etc/kubernetes/audit-webhook.yaml. Replace <wazuh_server_ip> with the IP address of your Wazuh server
3. Edit the Kubernetes API server configuration file and add the highlighted lines under the relevant sections
Create detection rules on the Wazuh server
We create a base rule 110002 that matches all Kubernetes audit events received via the webhook listener. Rule 110003 alerts Kubernetes “create” events, while rule 110004 alerts Kubernetes “delete” events.
1. Add the following rules to the Wazuh server at /var/ossec/etc/rules/local_rules.xml
2. Restart the Wazuh manager to apply the rules
Test the configuration
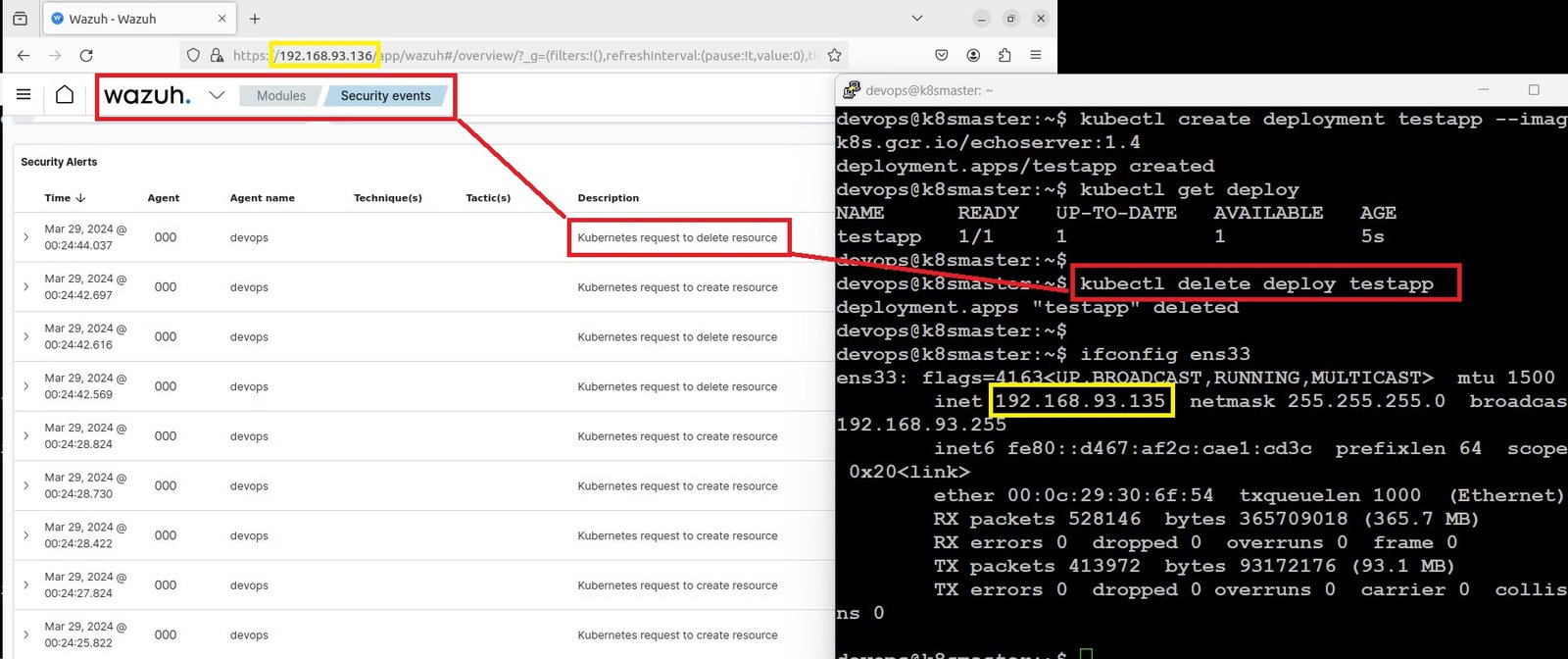
Test the rules by creating and deleting a deployment on the Kubernetes cluster as below
To Explore More in DevSecOps- Read More :
What is Wazuh Archietecture & Components?
Role of Wazuh as SIEM Tool in DevSecops and Kubernetes
Roles and Responsibilities of DevSecOps Engineer
DevSecOps Tool-Static Application Security Testing (SAST) tools
DevSecOps Tool-Dynamic Application Security Testing (DAST) Tools
DevSecOps Tool-Software Composition Analysis (SCA) Tools
DevSecOps Tool-Container Security Tools in DevSecOps
DevSecOps Tool-Infrastructure as Code (IaC) security Tools
DevSecOps Tools – Secrets Management Tools
DevSecOps Tools – Vulnerability Management Tools
DevSecOps Tools – Security Orchestration, Automation, and Response (SOAR) Tools
DevSecOps Tools – Security Information and Event Management (SIEM) tools