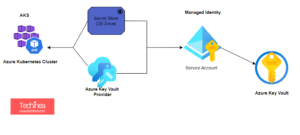
Azure Managed Identity is a feature provided by Microsoft Azure that helps securely manage credentials used by applications and services to authenticate with various Azure resources. Traditionally, developers have had to manage credentials such as usernames and passwords or access keys explicitly within their code or configuration files. However, this approach can be cumbersome, error-prone, and poses security risks if credentials are mishandled or exposed.
Managed Identity simplifies this process by allowing Azure services to automatically obtain and manage the credentials necessary for authenticating with other Azure services and resources. It provides a secure way for applications and services running on Azure to authenticate without needing to explicitly manage credentials.
Here’s how Azure Managed Identity typically works:
Identity Creation: When you enable Managed Identity for an Azure service, such as a virtual machine, Azure App Service, or Azure Function, Azure creates a managed identity for that service in the Azure Active Directory (Azure AD) tenant associated with the Azure subscription.
Service Principal: Under the hood, Azure creates a service principal in Azure AD for the managed identity. This service principal represents the identity of the Azure service or resource and allows it to authenticate with other Azure resources.
Role-Based Access Control (RBAC): You can then assign roles and permissions to the managed identity using Azure RBAC. This ensures that the managed identity has the appropriate level of access to the Azure resources it needs to interact with, following the principle of least privilege.
Authentication: When the Azure service needs to authenticate with another Azure resource, it can use its managed identity to obtain an access token from Azure AD. This access token is then presented to the target Azure resource, allowing the Azure service to access the resource securely.
Automatic Credential Rotation: Managed Identities also support automatic credential rotation, which enhances security by regularly rotating the credentials used for authentication without any manual intervention required.
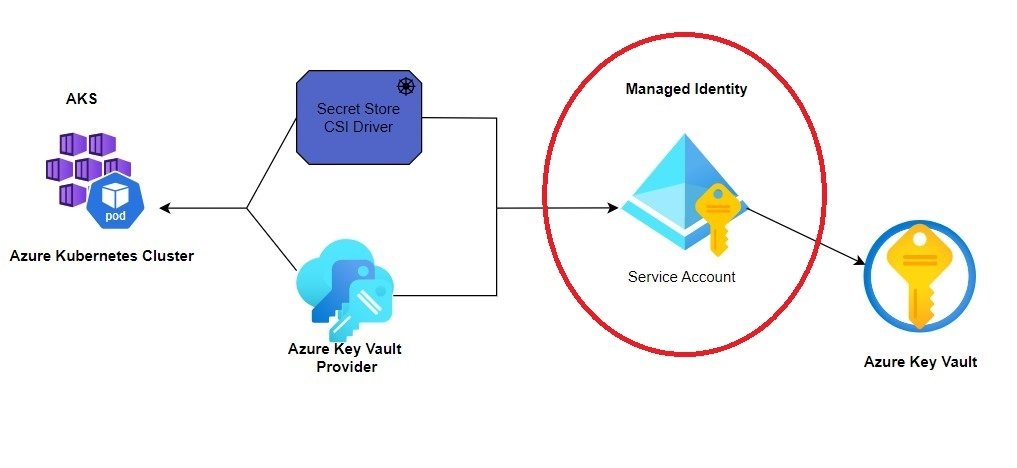
Here’s a more in-depth explanation of Azure Managed Identity:
Purpose: Managed Identity addresses the challenge of securely accessing Azure resources without the need to embed credentials within your code or manage service principals manually. It provides a way for Azure services to authenticate themselves to other Azure services, eliminating the need for developers to manage credentials.
Types of Managed Identities:
- System-assigned Managed Identity: This type of Managed Identity is tied directly to an Azure service instance, such as a Virtual Machine (VM), Azure Function, or Azure App Service. Azure automatically creates and manages the identity on behalf of the service. The identity lifecycle is tied to the lifecycle of the associated Azure resource.
- User-assigned Managed Identity: With this type, you create a Managed Identity as a standalone Azure resource, separate from any specific Azure service. You can then assign this identity to one or more Azure resources, allowing them to use the identity for authentication.
Authentication Process: Managed Identities use Azure Active Directory (Azure AD) for authentication. When an Azure resource with a Managed Identity tries to access another Azure resource, it requests a token from Azure AD. Azure AD validates the identity and issues a token, which the resource can use to access the requested resource.
Role-Based Access Control (RBAC): Managed Identities adhere to RBAC principles, allowing you to grant specific permissions to the identity. You can assign roles to the Managed Identity at the subscription, resource group, or resource level, controlling what actions it can perform within your Azure environment.
Benefits:
- Enhanced Security: Managed Identities reduce the exposure of credentials, as they eliminate the need to store credentials in code or configuration files.
- Simplified Management: By automating identity management, Managed Identities reduce administrative overhead associated with credential management.
- Scalability and Flexibility: Managed Identities seamlessly integrate with other Azure services, providing a scalable and flexible authentication solution for cloud applications and services.
Use Cases: Managed Identities are commonly used in scenarios such as accessing Azure Key Vault secrets, connecting to Azure SQL Database, accessing Azure Storage, and calling Azure REST APIs securely.
By leveraging Azure Managed Identity, developers can build more secure and streamlined applications and services on Azure without having to manage credentials directly. It helps improve security posture, reduces the risk of credential exposure, and simplifies the development and management of cloud-native applications.