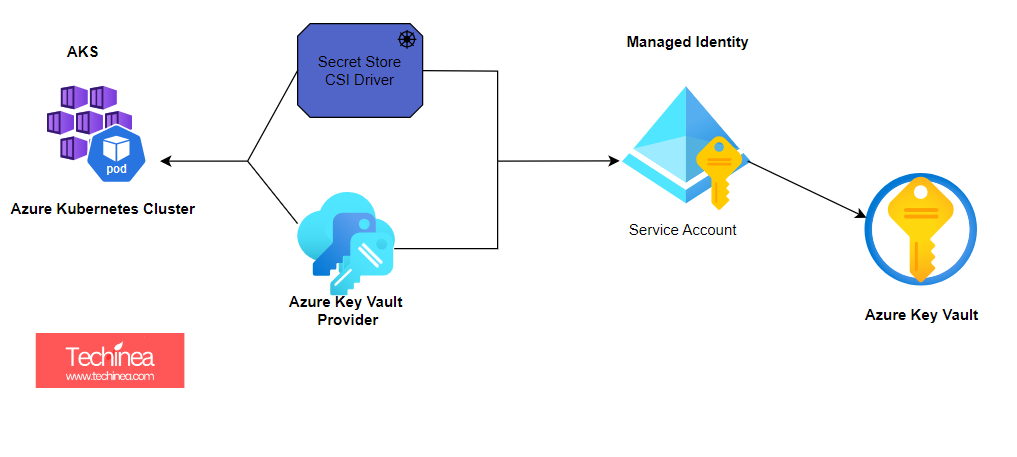
Azure Key Vault is a cloud service offered by Microsoft Azure that securely stores and manages sensitive information such as cryptographic keys, certificates, and secrets. It helps developers to control access to sensitive data by providing centralized storage and management of keys, certificates, and secrets.
Here are some key features and functionalities of Azure Key Vault:
Secure Storage: Azure Key Vault provides a secure repository for cryptographic keys, certificates, and secrets by storing them in Hardware Security Modules (HSMs). These HSMs are managed by Microsoft and are FIPS 140-2 Level 2 validated.
Key Management: Developers can create, import, and manage cryptographic keys used for encryption, decryption, signing, and verification.
Certificate Management: Azure Key Vault supports the management of X.509 certificates, including the ability to import, renew, and revoke certificates.
Secrets Management: It enables the secure storage and management of application secrets such as database connection strings, API keys, and passwords.
Access Control: Azure Key Vault integrates with Azure Active Directory (AAD) to manage access to keys, certificates, and secrets. Access policies can be defined to grant specific permissions to users and applications.
Audit Logging: Azure Key Vault logs all access and usage of keys, certificates, and secrets, providing an audit trail for compliance purposes.
Integration: It seamlessly integrates with other Azure services such as Azure Virtual Machines, Azure Functions, Azure App Service, Azure Kubernetes Service (AKS), and more, allowing applications to securely access keys, certificates, and secrets without exposing sensitive information.
By using Azure Key Vault, organizations can enhance the security of their applications and data by centralizing and securing the management of cryptographic keys, certificates, and secrets.
High level Configuration steps:
1. Enable Secret Store CSI Driver to kubernetes(AKS) pods
2. Install Secret Store Provider (Azure Provider)
2. Create a Azure Key Vault with Azure RBAC Role (Key Valut Administrator) & assign user to it.
4. Configure Azure Managed identity
5. Define the steps to mount the volume with CSI/Driver (secrets-store-.csi.k8s.io)/Volume Mounts in the kubernetes manifests(yaml files)